For the full specification of Isap we refer to the official specification document: Isap v2.0
Isap's Authenticated Encryption Mode
Isap is a sponge-based mode of operation for authenticated encryption and is designed with a focus on robustness against various kinds of implementation attacks. The recommended key, tag and nonce length is 128 bits. Isap can be instantiated with either Ascon-p or Keccak-p[400] as the underlying permutation, each with two possible parameterizations, which gives the following 4 instantiations:
Proposed instantiations of Isap
| Cipher | Permutation | Bit size of | Rounds | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| n | rH | rB | sH | sB | sE | sK | |||||
| Isap-A-128a | Ascon-p | 320 | 64 | 1 | 12 | 1 | 6 | 12 | |||
| Isap-K-128a | Keccak-p[400] | 400 | 144 | 1 | 16 | 1 | 8 | 8 | |||
| Isap-A-128 | Ascon-p | 320 | 64 | 1 | 12 | 12 | 12 | 12 | |||
| Isap-K-128 | Keccak-p[400] | 400 | 144 | 1 | 20 | 12 | 12 | 12 | |||
The encryption/decryption process consists of the following building blocks:
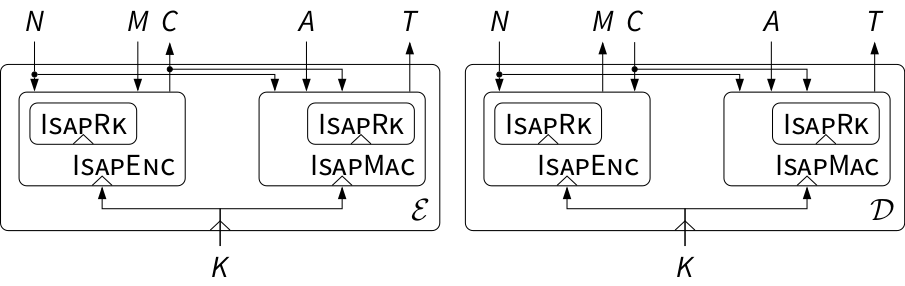
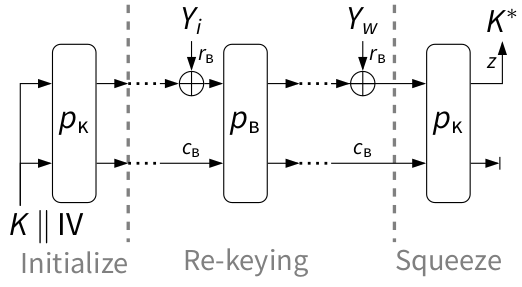
- IsapRk: Derives the session keys K*A or K*E from the long term key K.
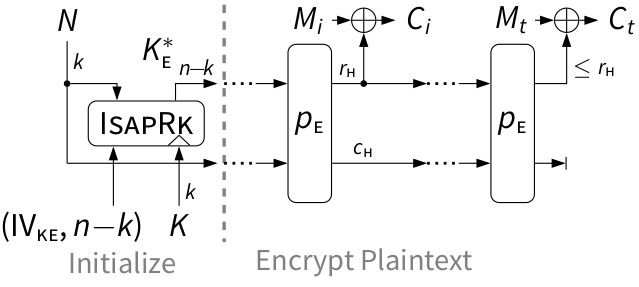
- IsapEnc: Stream encryption of message blocks Mi...t using K*E .
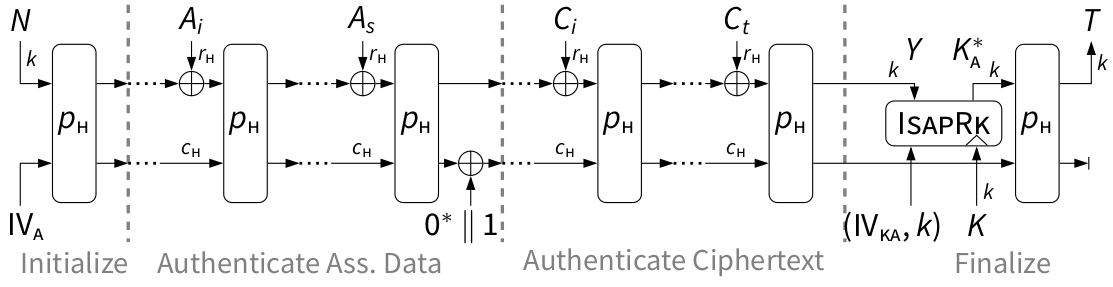
- IsapMac: Absorbs associated data blocks Ai...s and ciphertext blocks Ci...t and generates tag T using K*A .
These building blocks are used together with Key K, Nonce N, Associated Data A, Ciphertext C, and Tag T in an Encrypt-then-MAC fashion to perform authenticated encryption 𝓔 or authenticated decryption 𝓓:
Authenticated encryption 𝓔 and decryption 𝓓 in Isap [tex]
IsapRk, IsapEnc, and IsapMac are defined as follows:
The re-keying function IsapRk [tex]
The stream encryption with re-keying IsapEnc [tex]
The suffix-keyed sponge with re-keying IsapMac [tex]